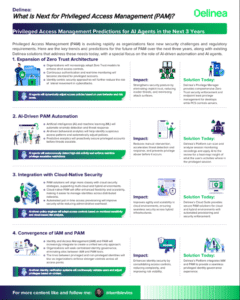
Privileged Access Management Predictions for AI Agents in the Next 3 Years
Organizations will increasingly adopt Zero Trust models to enforce strict access controls.
AI-Driven PAM Automation
Artificial intelligence (AI) and machine learning (ML) will automate anomaly detection and threat response.
Integration with Cloud-Native Security
PAM solutions will align more closely with cloud security strategies, supporting multi-cloud and hybrid environments.
Convergence of IAM and PAM
Identity and Access Management (IAM) and PAM will increasingly integrate to create a unified security approach.
Growth of Non-Human Identity Management
The rise of non-human identities, such as service accounts, bots, and APIs, will drive demand for machine identity
management.
Passwordless Authentication and MFA Enhancements
Organizations will shift toward passwordless authentication to
reduce reliance on static credentials.


Regulatory and Compliance Enhancements
Increased regulatory requirements will drive organizations to
adopt PAM best practices.
Compliance frameworks will demand greater transparency and auditability of privileged access.
Greater Emphasis on Endpoint Privilege Management
Organizations will enforce least privilege access policies at the
endpoint level to minimize attack surfaces.
Endpoint privilege management will integrate with broader
PAM strategies to ensure comprehensive security.
 Conclusion
Conclusion

Over the next three years, Privileged Access Management will continue to evolve, driven by technological advancements
and cybersecurity threats. Organizations must stay ahead by embracing AI-driven automation, Zero Trust security
models, and improved identity governance to protect critical assets and ensure compliance. AI agents will play a pivotal
role in automating security decisions, enforcing dynamic access controls, and proactively mitigating risks. Delinea
provides cutting-edge PAM solutions that enable organizations to meet these evolving security needs today.
To be minted
Attributes



 Privileged Credential Activity Reporting Services
Privileged Credential Activity Reporting Services

Scheduled Reports
Creating New Schedules for Reports To create a schedule for a report,
click the Schedules tab on the Report View page: Click the Create
Schedule button. The Report Schedule page appears: Configure the
report settings as listed in Editing Schedule Settings Click the Save
button.
 Question & Answars
Question & Answars

Frequently Asked Questions
Secret Server includes many pre-configured reports that you can run or use
as templates for creating custom reports. Below are the reports shipped
with current release of Secret Server: Unless otherwise designated, reports
listed are available in all editions.
As version 7.0, Secret Server allows creation of Reports using custom SQL.
Reporting supports embedding certain parameters into the SQL to give the
viewer controls to dynamically change the report.
The reporting interface comes with a set of standard reports. These reports
include a variety of 2D and 3D charting and graphing components and a full
grid of data. Some of the reports are purely data detailed and have no charts.
You can also create your own reports based on any Secret Server data.
Before running reports and audits, you must create something to report
on—to that end: Import a few accounts or create secrets manually Rotate
passwords a few times View a couple of your secrets This generates enough
audit logs to provide meaningful outputs in your reports: Security Hardening
Repor.
Click the Reports menu item. The Reports page appears: Click the link for the
desired report. Its page appears: Click the button in the top right of the item
table. The download popup appears: Click the Export dropdown list to choose
which data to download.
In addition to the user audit and individual secret audit, the reporting feature
provides a series of activity, user, and secret reports. See Built-in Reports
for the most up-to-date list of reports included. Users can also create their
own, custom reports.
To view auditing for all actions performed on a report, do the following: Click
Reports from the left navigation panel. Click the report for which you wish to
view an audit. At the far right end of the page, click the button labeled View
Audit.
If there are requirements around protecting potentially personally identifying
information when running reports or viewing recorded sessions, you can
enforce that another user has authorized you by enabling dual control for a
secret or Report.
To view a user audit report: From the Reports page, click the User Audit tab.
From the dialog on the tab, select a user and a date range to view. Click
Search History to view the user's audit trail. The audit search displays results
for all the secrets the selected user has viewed or edited during.
Overview There are 3 reasons for Delinea products to call home—when:
Checking for available updates Activating licenses Reporting anonymized
usage metrics Each of these communications is explained below and can be
disabled or avoided. Checking for and Downloading Updates Frequency: Once
per day The...
This topic is a one-stop resource for Secret Server developers. It points to
topics, as well as legacy knowledgebase articles. See the main APIs and
Scripting section too. Custom Reports Creating a Custom Report Using
Dynamic Parameters in Reports General Scripting Configuring CredSSP for
WinRM...
Secret Server provides comprehensive auditing features to help
organizations meet regulatory requirements and ensure security
compliance. Here is an overview of the auditing capabilities in Secret Server:
Local Auditing Secret Server locally audits all actions taken within the
system.
 Our Goals
Our Goals

Roadmap
PHASE 01
The standard chunk of Lorem Ipsum used since the 1500s is reproduced below for those interested. Sections 1.10.32 and 1.10.33 from "de Finibus Bonorum et Malorum" by Cicero are also reproduced.
PHASE 02
There are many variations of passages of Lorem Ipsum available, but the majority have suffered alteration in some form, by injected humour
PHASE 03
The standard chunk of Lorem Ipsum used since the 1500s is reproduced below for those interested. Sections 1.10.32 and 1.10.33 from "de Finibus Bonorum et Malorum" by Cicero are also reproduced.
PHASE 04
The standard chunk of Lorem Ipsum used since the 1500s is reproduced below for those interested. Sections 1.10.32 and 1.10.33 from "de Finibus Bonorum et Malorum" by Cicero are also reproduced.
PHASE 05
On the other hand, we denounce with righteous indignation and dislike men
PHASE 06
Reproduced below for those interested. Sections 1.10.32 and 1.10.33 from "de Finibus Bonorum et Malorum" by Cicero are also reproduced.
 Question & Answars
Question & Answars

Frequently Asked Questions

Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
It has roots in a piece of classical Latin literature from 45 BC, making it over 2000 years old. Richard McClintock, a Latin professor at Hampden-Sydney College in Virginia, looked up one of the more obscure Latin words, consectetur cites of the word in classical literature.
Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
 As seen In
As seen In

Our Partners



 Features
Features

Secret Server On-Premises Features by Version General Access Control See Gain control over web apps and cloud management platforms for more information. Password hiding refers to techniques used to prevent passwords from being displayed or stored in plain text, thereby protecting them from being.
 Secret Server Role Permissions List
Secret Server Role Permissions List

Overview Secret Server uses role-based access control (RBAC) to regulate permissions. The roles are assigned to users or groups. A complete list of the permissions available to roles appears below: To see the built-in roles and what permissions they possess, click the desired role link on the Admin.
 Secret Server Cloud
Secret Server Cloud

Secret Server Cloud is a scalable, multi-tenant cloud platform that offers the same robust features as the on-premise Secret Server Professional edition. Hosted on the Microsoft Azure platform, Secret Server Cloud ensures that all backend services, databases, and redundancy are securely managed by...
Contact Info
Our Info
- David Hollerbach Commercial Account Executive (TOLA)


